Cellular Data Extraction and Reporting
From custom designed exploits that bypass the latest cellular security to recovering messages from applications that promise “they are only available for a short time”. We lead the industry in data recovery. Our Firm is not limited by what commercially available forensic tools can accomplish. Our staff has the skillset to push the boundaries of modern forensics while maintaining court approved methodologies. Chances are, the competition’s tool makers have utilized our staff to write their code or handle complicated extractions for their top tier clients. From divorces to serial killers, we have been there and done that.
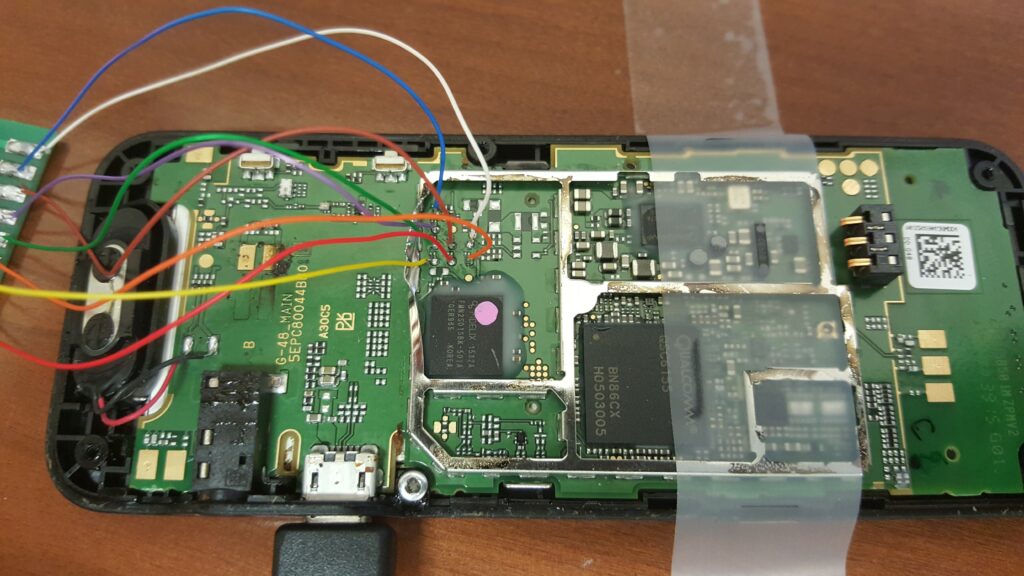
Joint Test Action Group (JTAG)
JTAG (Joint Test Action Group) is also known as the IEEE 1149.1 standard. JTAG is an advanced level data acquisition method which involves connecting to Test Access Ports (TAPs) on a device and instructing the processor to transfer the raw data stored on connected memory chips.
In System Programming (ISP)

In-system programming, also called in-circuit serial programming, is the ability of some programmable logic devices, microcontrollers, and other embedded devices to have their firmware extracted and or programmed while installed in a complete system, rather than requiring the chip to be removed in order to forensically acquire the embedded data.
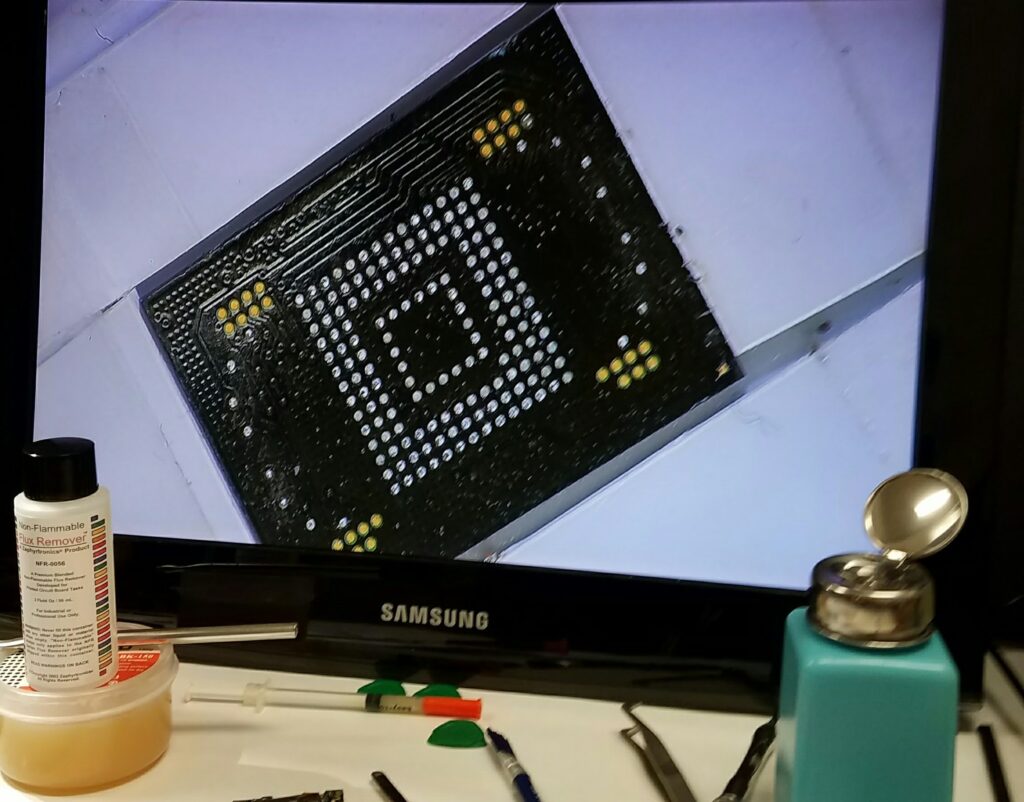
Chip Off Extraction
Chip–off is an advanced digital data extraction method and analysis technique which involves physically removing flash memory chip(s) from a subject device and then acquiring the raw data using specialized equipment. Our in house forensic expert was the first technician in the world to apply this technique with equipment acquisitioned by the National Aeronautics and Space Administration (NASA). This technique has since been certified by multiple Federal Agencies and taught by our SME to multiple Law Enforcement agencies all over the globe.